Understanding Triangulation Fraud
By utilizing the depths of the internet, criminals are targeting many different industries with eCommerce being a prime mark.
There was a time when organized crime had a face to it. Faces like Al Capone, Whitey Bulger, and John Dillinger, to name a few. These individuals had sophisticated organizations to handle their criminal activities and lived to make a profit.
Organized crime has become more anonymous, with no face or infamous figures. The reason for that is simple − the Dark Web − a collection of websites that are publicly visible but hide the IP addresses of the servers that run them. Anyone can visit them, but it is very difficult to decipher who is behind them. By utilizing the depths of the internet, criminals are targeting many different industries, with eCommerce being a prime mark. One of the more sophisticated eCommerce attack schemes, Triangulation Fraud, uses a network of mules to commit fraudulent transactions.
What is Triangulation Fraud?
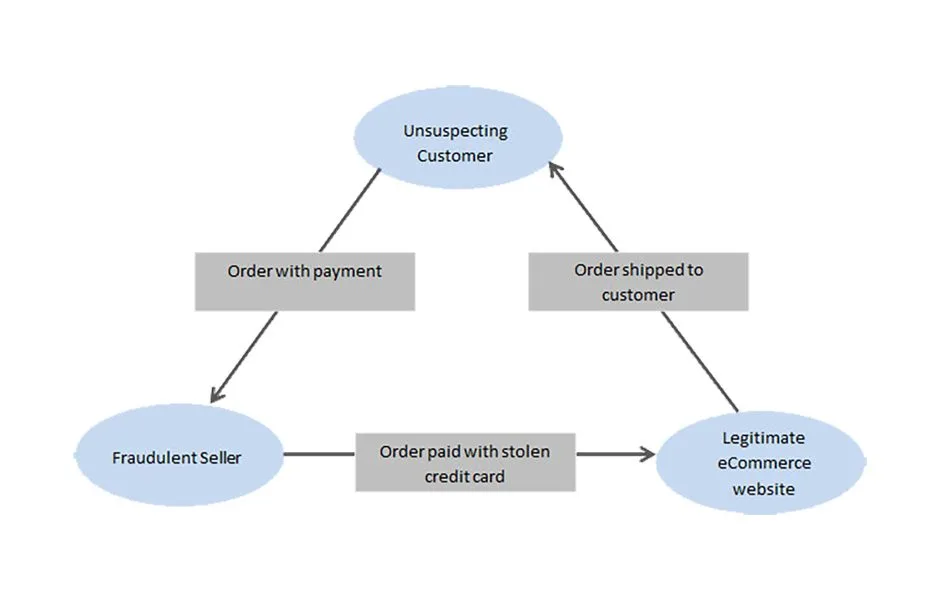
One of the lesser-known types of eCommerce fraud, triangulation fraud is a type of online shopping scam that typically involves three parties: a scammer, an unsuspecting customer, and a legitimate business. In this scheme, the fraudster sets up an online store and lists products for sale. When a customer orders, the scammer uses stolen credit card information to purchase the item from a legitimate third-party vendor and have it shipped directly to the customer.
The three points in this fraud are:
- Scammer’s Store: The fraudulent online store where customers place orders.
- Legitimate Vendor: A real, unsuspecting business that sells the product listed on the scammer’s store.
- Customer: The person who makes a purchase on the scammer’s store, unaware that the product is being sourced from a legitimate vendor using stolen financial information.
Triangulation scams are problematic because they can harm both the customer and the legitimate vendor. The customer may receive a product, but they are usually left unknowingly involved in a fraudulent transaction. The legitimate vendor, on the other hand, may suffer financial losses due to chargebacks and disputes.
Customers should be cautious when purchasing from unfamiliar online stores to avoid falling victim to triangulation fraud. Legitimate businesses, on the other hand, should employ security measures to detect and prevent fraudulent transactions.
How Triangulation Fraud Works
In the elaborate process of triangulation fraud, perpetrators initiate their scheme by establishing a fraudulent online store designed to mimic legitimate eCommerce platforms. With a polished appearance, often featuring stolen product images and descriptions, the fraudulent store attracts unsuspecting customers seeking enticing deals or appealing merchandise. Once a customer places an order on this deceptive platform, they unwittingly provide personal and payment information under the assumption of conducting a genuine transaction. Exploiting this trust, the fraudster proceeds to the next stage by utilizing stolen credit card information acquired through means such as data breaches or the dark web.
The fraudster identifies a legitimate third-party vendor selling the same product in a strategic move to obscure their illicit activities. Utilizing the unlawfully obtained credit card details, the scammer makes a seemingly legitimate purchase from this vendor, who remains unaware of the fraudulent nature of the transaction. The purchased product is then shipped directly from the unsuspecting vendor to the customer’s provided address, completing the triangulation fraud cycle. Throughout this process, the customer remains oblivious to the fraudulent nature of the transaction. At the same time, the legitimate vendor may only discover the deception when faced with chargebacks or disputes, resulting in financial losses and potential harm to their reputation. This sophisticated scheme underscores the need for both customers and legitimate businesses to be vigilant in the increasingly complex landscape of online transactions.
What are the Characteristics of Triangulation Fraud?
- Easily resalable products such as:
- Baby/Kid products: strollers, cribs, etc.
- Lego products
- Pet supplies
- Nutritional Supplements
- Tools
- Electronics
- Small appliances
- Baby/Kid products: strollers, cribs, etc.
- Clean data
- This is regarding the order’s credit card, billing, and shipping information. The criminal will generally make the order look as clean as possible to avoid raising suspicion.
- This is regarding the order’s credit card, billing, and shipping information. The criminal will generally make the order look as clean as possible to avoid raising suspicion.
- Questionable email addresses or email domains
- The billing name is John Smith. The email is sandy.connor@outlook.com

Risks and Consequences of Triangulation Fraud
Triangulation fraud has emerged as a sophisticated online scheme that ensnares unsuspecting customers and legitimate vendors in a complex web of deception. This fraudulent practice operates through a meticulous process involving the establishment of fake online storefronts, the exploitation of unwitting customers, and the manipulation of legitimate vendors. As we delve into the intricacies of triangulation fraud, it becomes imperative to comprehend the risks and consequences associated with this malicious activity. In this section, we explore the profound impact on both customers and legitimate vendors, shedding light on the unsuspecting individuals caught in the crossfire of this digital deception.
Impact on Legitimate Customers
Within the intricate landscape of digital transactions, the looming threat of triangulation fraud casts a pervasive shadow that extends beyond financial considerations. This type of fraud can profoundly impact unsuspecting customers.
- Unaware involvement in fraudulent transactions: Triangulation fraud, with its insidious nature, propels customers unwittingly into criminal activities. Despite their genuine intent to engage in legitimate purchases, customers find themselves inadvertently entangled in a scheme orchestrated by fraudsters. This raises significant concerns about financial security and introduces a psychological and emotional burden on those who discover their unintentional association with fraudulent endeavors.
- Potential financial losses: Vulnerability to financial losses becomes a stark reality for customers ensnared in the web of triangulation fraud. As their credit card information is exploited, they confront the prospect of unauthorized transactions, identity theft, and other financial consequences. The resolution of these issues often entails arduous processes, exacerbating the potential toll on the affected individuals.
Impact on Legitimate Retailers
Navigating the labyrinth of triangulation fraud places legitimate vendors in a challenging position, grappling with consequences that extend beyond the realm of finances. This section elucidates the severe implications faced by businesses inadvertently caught in the crossfire of this fraudulent scheme.
- Financial losses due to chargebacks: Legitimate vendors shoulder the weight of triangulation fraud through financial losses incurred via chargebacks. When customers uncover the fraudulent nature of transactions and initiate chargebacks, vendors find themselves in a precarious position, compelled to refund amounts for goods or services legitimately provided. This financial strain poses a substantial challenge to the economic stability of businesses unwittingly ensnared in the fraudulent web.
- Damage to reputation: The repercussions of triangulation fraud transcend mere financial losses for legitimate vendors, extending to the realm of reputation. Customers grappling with issues stemming from their transactions may associate negative experiences with the legitimate vendor, unaware that the wrongdoing lies with the fraudulent online store. The enduring impact on reputation can erode customer trust and brand loyalty, further complicating the aftermath for these unwitting businesses.
Understanding the multifaceted impact on customers and legitimate vendors is paramount for the development of effective strategies to combat triangulation fraud and safeguard the integrity of digital transactions.

Triangulation eCommerce Fraud Prevention
In the relentless battle against triangulation fraud, businesses must adopt robust prevention measures to safeguard their operations, protect their reputation, and ensure the trust of their customers. Here are strategic steps for businesses to fortify themselves against the deceptive complexities of triangulation fraud:
Implementing Fraud Detection Tools
Businesses should invest in and deploy sophisticated eCommerce fraud protection tools. These tools utilize advanced algorithms, machine learning, and analytics to scrutinize transaction data in real-time, identifying patterns indicative of fraudulent activities. Automated alerts can prompt immediate action, enabling businesses to intervene swiftly and mitigate potential financial losses. Regularly updating and fine-tuning these tools is crucial to stay ahead of evolving fraud tactics.
Enhancing Verification Processes for Online Transactions
Strengthening verification processes is imperative to weed out fraudulent transactions. Businesses should consider implementing multi-factor authentication, address verification systems, and other identity verification mechanisms. These measures add layers of scrutiny, making it more challenging for fraudsters to exploit the online transaction process. Verification steps should be seamlessly integrated into the customer experience to maintain efficiency while ensuring security.
Conducting Regular Audits and Assessments
Regular audits and assessments of online transactions and personal data can help businesses identify vulnerabilities and areas for improvement. This proactive approach allows for the identification of potential weak points in the system, enabling businesses to rectify issues before fraudsters can exploit them.
Employee Training and Awareness Programs
Equip employees with the knowledge and skills necessary to identify and respond to potential instances of triangulation fraud. Training programs should cover emerging eCommerce fraud statistics, red flags associated with suspicious transactions, and protocols for reporting and addressing potential threats. Creating a culture of awareness within the organization is critical to maintaining a united front against fraudulent activities.
Collaboration with Industry Partners and Information Sharing
Collaborating with other businesses, industry associations, and law enforcement agencies can enhance the collective ability to combat triangulation fraud. Establishing information-sharing channels about emerging threats and fraudulent tactics can provide businesses with valuable insights and early warnings.
Continuous Education and Adaptation
The dynamic fraud landscape requires businesses to stay abreast of evolving tactics. Continuous education and staying informed about the latest eCommerce fraud trends empower businesses to adapt their prevention measures accordingly. Regularly updating systems, protocols, and employee training ensures the organization remains resilient despite emerging threats.
By prioritizing these prevention measures, businesses can create a fortified defense against triangulation fraud, preserving the integrity of their operations and maintaining the trust of their customers in the ever-evolving digital marketplace.
Prevent Triangulation Fraud with Radial
Awareness stands as the first line of defense against the insidious nature of a triangulation fraud scheme. Customers must be discerning, conduct thorough research before engaging in online transactions, and remain vigilant in monitoring their financial statements. On the other hand, businesses must prioritize awareness within their organizations, ensuring that employees are well-equipped to recognize and respond to potential threats.
As part of this collective effort, we invite you to explore Radial’s cutting-edge solutions for triangulation fraud prevention, merchant fraud protection, and credit card fraud protection. Contact us to discover how Radial can fortify our business against the evolving threats of online fraud. Let’s secure the digital marketplace together for a resilient and trustworthy online experience.
Radial can help you prevent fraud.
